A common misconception within organizations that must comply with HIPAA is that if you’re a smaller health care organization, then a Breach won’t happen to you. Find out why this misconception is common, and why it isn’t true.
 One of the biggest hindrances to HIPAA compliance and breach protection is the belief that a breach won’t happen to you, and, unfortunately, many small health care organizations hold to this. Many health care providers think that because they work in a small office, hackers won’t be looking for them. But, that’s just not the case. Hackers will attack any network available that contains valuable information.
One of the biggest hindrances to HIPAA compliance and breach protection is the belief that a breach won’t happen to you, and, unfortunately, many small health care organizations hold to this. Many health care providers think that because they work in a small office, hackers won’t be looking for them. But, that’s just not the case. Hackers will attack any network available that contains valuable information.
Plus, breaches aren’t just hacking attempts. A breach can occur when an employee does something as simple as sending a fax to the wrong number. According to the U.S. Department of Health and Human Services (HHS), “A breach is, generally, an impermissible use or disclosure under the Privacy Rule that compromises the security or privacy of the protected health information [PHI].” So, anytime PHI is purposefully or accidentally used or disclosed incorrectly, a breach has occurred and must be reported to the Office for Civil Rights (OCR).
There are a couple exceptions to reporting. HHS states that the incident is not a breach if the covered entity or business associate can demonstrate that “there is a low probability that the protected health information has been compromised based on a risk assessment of at least the following factors:
1. The nature and extent of the protected health information involved, including the types of identifiers and the likelihood of re-identification;
2. The unauthorized person who used the protected health information or to whom the disclosure was made;
3. Whether the protected health information was actually acquired or viewed; and
4. The extent to which the risk to the protected health information has been mitigated.”
If the organization cannot show that the would-be breach falls into one of these categories as low to no risk for the PHI to be misused or to have been seen or acquired by an impermissible person, then it is a breach that must be reported to the OCR. And, if the breach affects more than 500 individuals, the health care organization must report the breach to the media and to all individuals affected.
The difference in breach reporting based on the number of individuals affected is a huge contributor to the belief that smaller organizations don’t have breaches. Because breaches aren’t reported in the news if they affect fewer than 500 people, organizations rarely hear about breaches happening at smaller organizations. Many small offices do not even have 500 patients. All this to say, even if you don’t hear about these smaller breaches in the news, they’re happening.
Aside from requesting information through the freedom of information act, the only real information available is through a breach report that the OCR provides for the government to review. The report is compiled every two years and lags behind by at least a year. So the most recent data available is from 2014, covering 2011 to 2014. However, looking at the trends for those four years, there has been a successive increase in breach reports, and that includes breaches that affect less than 500 people.
Here’s some of the OCR’s data:
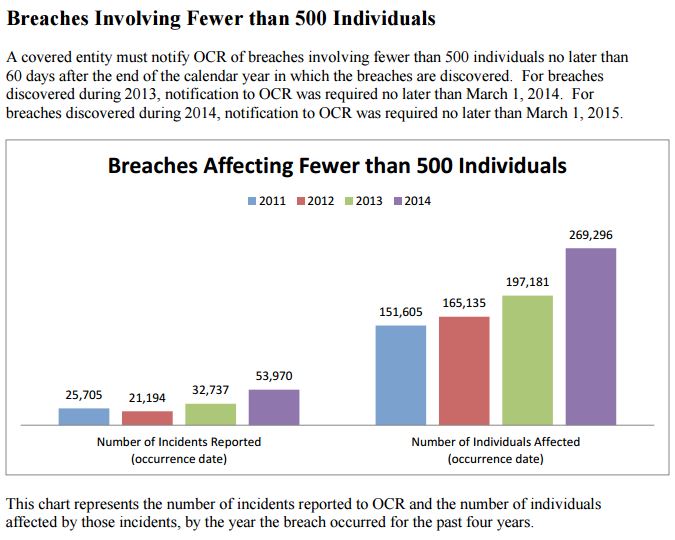
As seen in the image above, the number of incidents reported has risen, as well as the number of patients affected.
Why is a Breach likely to happen to all organizations regardless of size?
Hackers will attempt to gain access anywhere they can, and the smaller organizations are perfect for that, since they tend to have less money available for protecting their networks. Smaller organizations also often use free email systems, which tend to have fewer protections in place, meaning a malicious email may slip through the spam filter more easily.
Also, many smaller offices have less time and fewer resources available for staying up-to-date on HIPAA compliance and methods in which breaches occur. The smaller office with the office manager working as the receptionist and HIPAA officer typically doesn’t have much background in HIPAA or the time to figure it out on his or her own. And, the doctor who can barely afford to pay for that office manager/receptionist probably doesn’t realize how his or her office is noncompliant with HIPAA and at risk. This doctor also probably doesn’t have a few thousand dollars to spend on updated training, a new risk assessment tool, or cybersecurity services.
And so, these small offices oftentimes choose to live with the risk of a breach and OCR fine. Unfortunately, viewing HIPAA compliance in this way is like playing the game of not having health insurance. Sure, you are healthy now, but what happens if you get hit by a motorist without liability insurance. Then, you are stuck paying all the bills.
In much the same way, not staying up to date on HIPAA will cost you in the long run if you have a breach. The minimum penalty for a breach is $100 per violation. That’s just for an unknown breach, like the accidental fax mentioned earlier. If there is willful neglect, like not having a risk assessment or other HIPAA compliance practices actively in place, it jumps up to $10,000-per-violation minimum. That could potentially cost a doctor his practice if he can’t afford the fine.
Stay HIPAA Compliant
Don’t risk a life-re-defining breach; get started today with HIPAAgps and stay HIPAA compliant. Our simple, online tool is cost effective and will help your organization reduce your risk of breaches and large fines as we help guide you through the many HIPAA requirements.

Recent Comments